
Mining cryptocurrencies can be very lucrative, but making a profit is challenging without the means to cover large costs.
Cryptojacking is the unauthorized use of someone else’s computer to mine cryptocurrency. Hackers can load cryptomining code on the computer, or they can infect a website or online ad with code that runs automatically once loaded in the victim’s web browser.
In this blog, we will discuss how cryptojacking works, how to detect it, and some ways to protect your machine from being hijacked.
How Does Cryptojacking Work?
The cryptomining process is done by crypto miners, who use high-powered computers and special hardware to compute and use a hash function that allows the block to join the blockchain, earning crypto in return. Mining can take a lot of hardware resources, mainly in processing power.
Hackers looking for a payday will try to lighten the resource load by stealing the resources of someone else’s machine to mine for digital currency. Cybercriminals have three primary ways to get access to a computer to mine cryptocurrency: phishing, browser-based, or through the cloud.
The more common way is to trick users into loading cryptomining software on their computers. This is usually done through phishing techniques. Hackers will send an email to users that looks legitimate, encouraging them to click on the link. Once clicked, the deceptive link will run a script that runs in the background as the user works.
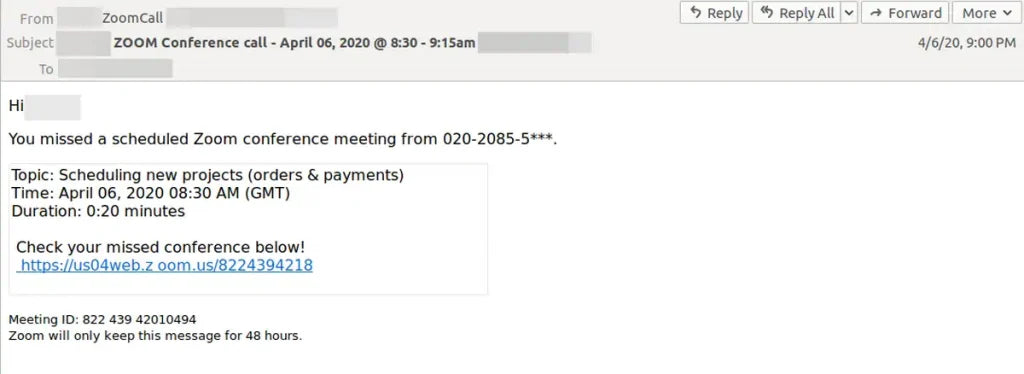
Another common method for crypto hackers is to inject code on website or an ad that is delivered to multiple websites. In this case, a user will have to visit the website that is infected, or the malicious ad pops up on their browsers. Whether they access a website or see the ad, the cryptojacking script automatically executes, running in the background.
Cybercriminals can also initiate cryptojacking attacks through the cloud. This is more common in businesses with large cloud infrastructure. In this case, hackers will search through an organization’s files. Then they use code to access their cloud services. Once they have access, hackers will begin taking all the resources they need to mine digital currencies.
How Can I Detect Cryptojacking?
Since most of the damage done to computers with cryptojacking is done to hardware, you will want to monitor any sudden changes in performance with your computer. The first signs of a potential cryptojacking attempt are a slower computer. Day-to-day activities will take longer than usual to run.
You may notice your computer is running hotter than usual. The resource-intensive process of cryptojacking can cause hardware to overheat. Also, related to overheating are fans that run longer than they should to cool down the system.
The biggest resource that is used in bitcoin mining is processing power, so if you notice there are performance issues, it is a good idea to monitor CPU usage. You can do this by using the Activity Monitor (Mac) or Task Manager (Windows). If you see that there is a large uptick (90% and above is cause for concern) in CPU usage when visiting a website with little or no media content, there could be cryptojacking script running.
When browsing the web, keep an eye on the different websites you use. Cybercriminals are looking for websites where they can embed cryptomining code. Monitor the websites you use for any changes to web pages or if they're are out of the ordinary changes to access options.
How to Prevent Cryptojacking
The best line of defense in preventing these types of attacks is having a solid antivirus program. An antivirus program should include emergency and periodic scans, frequent scans, and it should have a comfortable user interface. It should be light on resources, so it does not slow down your computer’s other important programs.
It is also good practice to install the latest software updates and patches for your operating system and all applications — especially those concerning web browsers. Developers release updates and patches that address vulnerabilities and flaws.
Safe web browsing is crucial to preventing cryptojacking attempts. There are web browser extensions like No Coin and Anti Miner that can help block cryptojackers across the web. Since cryptojacking scripts are implemented through online ads, installing an ad blocker is a great way to slow them down. Ad blockers like Ad Blocker Plus or uBlock Origin can both detect and block cryptojacking code.
If necessary, you may want to disable JavaScript. JavaScript is a common coding language used in these types of attacks. Disabling JavaScript can prevent cryptojacking code from infecting your computer. Please note that JavaScript also helps other websites function; disabling it might block many of the functions you need to run the site properly.
Wrapping Up
While other cybersecurity attacks will look to attack a machine for files or sensitive data, the only purpose of cryptojacking is to steal the physical power of a computer. The positive note about these attacks is they require some form of user interaction to be initiated.
Thankfully, cryptojacking attempts are easier to recognize because they will immediately affect PC performance.
With the everyday use of computers and the internet, it can become easy to lose track of the many websites and applications that have become a part of daily life. By monitoring any sudden changes, scanning for malware, running updates and patches consistently, you can add a layer of defense to protect your machine from hackers.






















